Millions Stolen: Inside The Office365 Executive Email Hack

Table of Contents
Understanding the Tactics Used in Office365 Executive Email Hacks
Attackers employ increasingly sophisticated tactics to breach Office365 executive email accounts. Understanding these methods is the first step in effective prevention.
Spear Phishing and Impersonation
Spear phishing is a highly targeted form of phishing that focuses on specific individuals, often executives. Attackers meticulously research their targets, crafting convincing emails that mimic trusted sources like colleagues, clients, or even the CEO.
- Example Subject Lines: "Urgent Payment Required," "Confidential Contract Attached," "Important Information Regarding [Project Name]."
- Attachments: Malicious documents (e.g., Word files with macros) or links leading to credential-harvesting websites.
- Social Engineering: Attackers leverage psychological manipulation to bypass security awareness. They might create a sense of urgency or leverage a known relationship to pressure the recipient into action.
Credential Stuffing and Brute-Force Attacks
These methods rely on automated tools to try various username and password combinations.
- Credential Stuffing: Attackers use stolen credentials from data breaches on other platforms to attempt logins to Office365 accounts.
- Brute-Force Attacks: Attackers use software to systematically try different password combinations until they find the correct one.
- Prevention: Implementing strong password policies, enforcing multi-factor authentication (MFA), and using password managers significantly reduces the effectiveness of these attacks. Unique and complex passwords are essential.
Exploiting Vulnerabilities
Attackers may exploit vulnerabilities in Office365 configurations or third-party applications.
- Legacy Protocols: Outdated protocols like POP3 and IMAP can be vulnerable to compromise.
- Unpatched Software: Failing to update software regularly leaves systems open to known exploits.
- Compromised Third-Party Apps: Attackers might target less secure third-party applications integrated with Office365 to gain unauthorized access.
The Financial and Reputational Ramifications of Successful Hacks
The consequences of a successful Office365 executive email hack extend far beyond the initial financial loss.
Direct Financial Losses
Direct financial losses can be catastrophic.
- Fraudulent Wire Transfers: Attackers can redirect funds to their accounts through manipulated invoices or payment requests.
- Invoice Redirection: Hackers intercept legitimate invoices, altering payment details to siphon off funds.
- Real-World Examples: Numerous cases have documented millions of dollars stolen through compromised executive email accounts. The impact on company finances and investor confidence can be devastating.
Reputational Damage
The damage to an organization's reputation can be long-lasting.
- Loss of Trust: A successful hack erodes trust with customers, partners, and investors.
- Legal Repercussions: Organizations face potential lawsuits and regulatory fines for failing to protect sensitive data.
- Employee Morale: Data breaches can significantly impact employee morale and productivity.
Effective Strategies to Prevent Office365 Executive Email Hacks
A multi-layered security approach is crucial to prevent Office365 executive email hacks.
Multi-Factor Authentication (MFA)
MFA adds an extra layer of security, significantly reducing the risk of unauthorized access.
- Methods: One-Time Passwords (OTP), biometric authentication, and security keys.
- Effectiveness: Even if credentials are stolen, MFA prevents attackers from accessing the account without the second factor.
Security Awareness Training
Educating employees is paramount.
- Training Methods: Regular phishing simulations, interactive training modules, and awareness campaigns.
- Frequency: Regular refresher training is crucial, as attacker tactics constantly evolve.
Robust Password Policies and Management
Strong passwords are the foundation of good security.
- Complexity: Enforce password complexity requirements (length, character types).
- Password Managers: Encourage the use of password managers to generate and securely store strong, unique passwords.
- Regular Changes: Implement regular password change policies.
Regular Security Audits and Penetration Testing
Proactive vulnerability identification is critical.
- Audits: Regular security audits identify weaknesses in your systems and processes.
- Penetration Testing: Simulates real-world attacks to uncover vulnerabilities before attackers can exploit them.
Email Security Solutions
Advanced email security solutions offer additional protection.
- Features: Email filtering, anti-spam, and anti-phishing capabilities can detect and block malicious emails.
- Solutions: Numerous vendors offer robust email security solutions tailored to organizational needs.
Conclusion: Protecting Your Organization from Office365 Executive Email Hacks
Office365 executive email hacks pose a significant threat to organizations of all sizes. The methods employed are sophisticated, and the consequences can be devastating, both financially and reputationally. A comprehensive security strategy incorporating MFA, robust password policies, regular security audits, employee training, and advanced email security solutions is essential. By proactively implementing these measures, you can significantly reduce your risk of falling victim to an Office365 executive email compromise and protect your valuable assets. For further information on enhancing your organization's cybersecurity posture, explore resources from reputable cybersecurity organizations and consult with security professionals. Don't wait until it's too late—protect your organization from the devastating impact of Office365 executive email hacks today.

Featured Posts
-
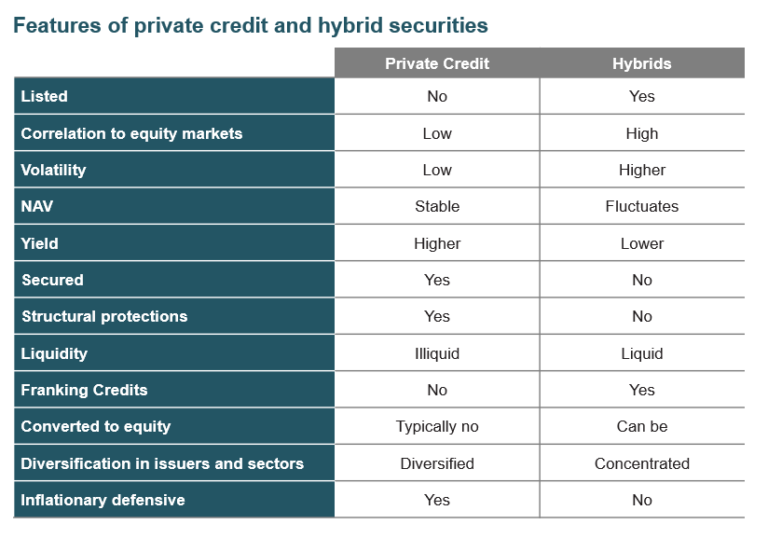 5 Dos And Don Ts For Landing A Private Credit Job
Apr 22, 2025
5 Dos And Don Ts For Landing A Private Credit Job
Apr 22, 2025 -
 Blue Origins Launch Abort Details On The Subsystem Failure
Apr 22, 2025
Blue Origins Launch Abort Details On The Subsystem Failure
Apr 22, 2025 -
 Razer Blade 16 2025 High End Performance In A Slim Design A Detailed Review
Apr 22, 2025
Razer Blade 16 2025 High End Performance In A Slim Design A Detailed Review
Apr 22, 2025 -
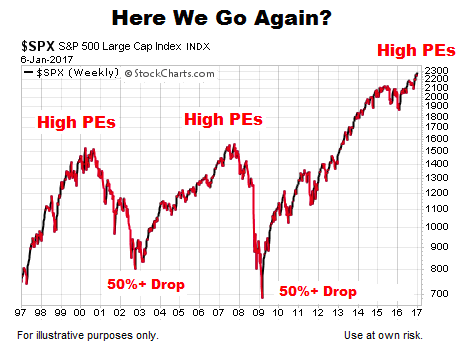 Understanding High Stock Market Valuations Insights From Bof A
Apr 22, 2025
Understanding High Stock Market Valuations Insights From Bof A
Apr 22, 2025 -
 Us Protests Against Trump Voices From Across The Nation
Apr 22, 2025
Us Protests Against Trump Voices From Across The Nation
Apr 22, 2025
